Cybersecurity Trends
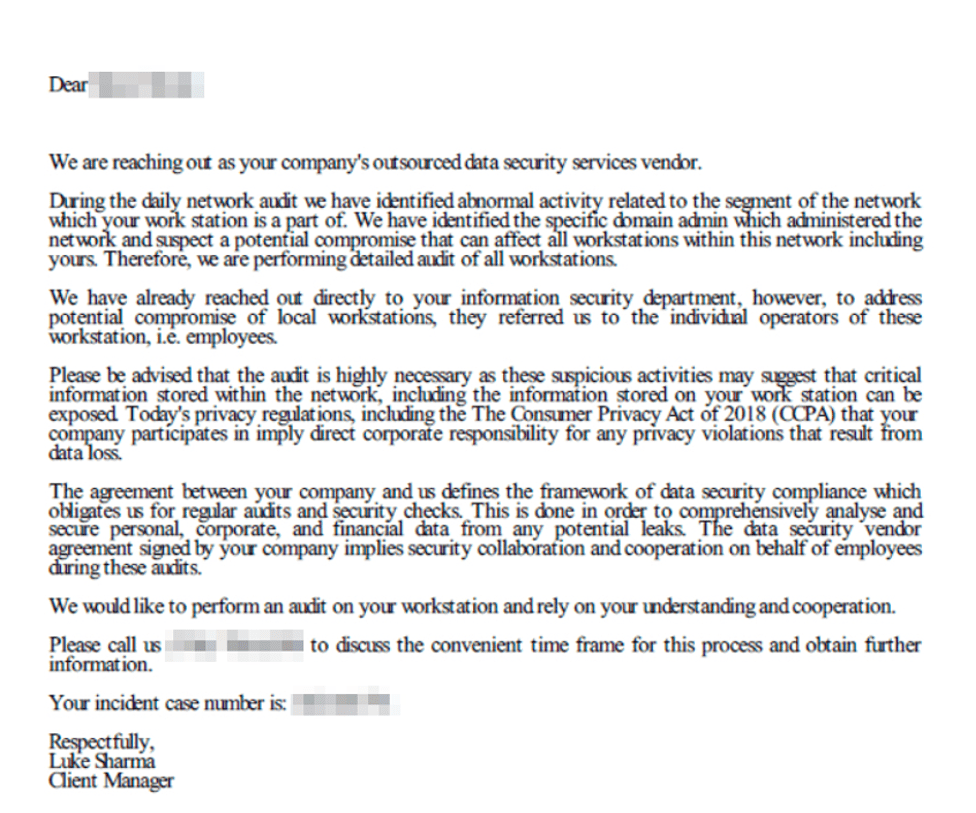
According to a report from Crowdstrike, well-known cybersecurity companies have become the most recent victims of impersonation attacks. The phishing campaign uses a fake e-mail, which looks as though it is coming from a real cybersecurity company, that then urges the user to call them.
Social engineering ensues with attempts to install a tool which would grant the attacker remote access. The report says “this is the first identified callback campaign impersonating cybersecurity entities and has higher potential success given the urgent nature of cyber breaches.” The exact companies being impersonated were not mentioned.
Education is Key
This is yet another example of why it is important to educate yourself and your workforce. Cybersecurity companies like F-Secure, Crowdstrike, etc. will not contact users directly. This e-mail, no matter how real it may seem, should immediately be seen as fake to the trained eye.
Fortunately, at Fizen Technology we have begun to educate our clients through a partnership with a Cybersecurity Training company. As users click on the simulated phishing attempts, they are told what they should have looked out for in the e-mail that was a signal that it was fake. They are then signed up for additional trainings.
 Common Phishing E-mail Techniques
Common Phishing E-mail Techniques
- Purporting to be from a trusted party
- Unsolicited. You did not expect such a message
- Not typical way to perform the function they want you or not typical function for you.
For Example:
- You never received faxes in an e-mail, but now you have received one
- Or the fax messages you have received in an e-mail, look different from the one you just received
- You never had anything to do with money wire transfer in the company. Now you received a message inquiring about that
- You have not sent any money transfers recently and received a message about it
- Money transfers that you completed in the past did not result in an e-mail that looks like the one you just received
Educate Employees
In summary, the best way to protect yourself and your business is to educate your employees on how to identify a cybersecurity attack and we can help with that.
 Common Phishing E-mail Techniques
Common Phishing E-mail Techniques